This post first appeared on Risk Management Magazine. Read the original article.

In February, the FBI issued an official warning to businesses about a new form of tax season scam in which fraudsters use social engineering attacks known as business email compromise (BEC) or CEO fraud to target W-2 forms. In the cases submitted to the Internet Crime Complaint Center, attackers spoofed or hacked the email account of a company’s high-level executive and sent an email to an employee in a human resources, bookkeeping or auditing function requesting employee W-2 forms.
With the employer name, employer ID, address, taxpayer address, Social Security number and information about 2016 wages and taxes withheld, W-2 forms give attackers all the information they need to file fraudulent tax refund requests. Phishers can also repurpose the valuable personal data in these forms to lodge better spearphishing attacks or simply sell the records online, where information security journalist Brian Krebs reports they are currently worth $4 to $20 apiece.
When W-2 phishing schemes first emerged last year, victims included Snapchat, Money Tree Lending Company, and Care.com. This season, the attacks have come back in force. “The W-2 scam is circulating earlier in the tax season and to a broader cross-section of organizations, including school districts, tribal casinos, chain restaurants, temporary staffing agencies, healthcare and shipping and freight,” according an urgent warning released by the Security Summit, a coalition of the IRS, state tax agencies and the tax industry. “Those businesses that received the scam email last year also are reportedly receiving it again this year.”
On Jan. 27, San Francisco solar firm Sunrun disclosed that a hacker posing as CEO Lynn Jurich obtained the W-2 forms of many of the firm’s 4,000 employees, including Social Security numbers and salary details, in a successful spearphishing attack. On Feb. 24, Boise, Idaho-based Amalgamated Sugar disclosed that a fraudster successfully mimicked the email address of CEO John McCreedy in search of W-2 forms, ultimately yielding the names, addresses, earned wages and Social Security numbers for 2,858 employees. Also in February, two school district employees in Manatee County, Florida, released more than 7,700 W-2 forms to a hacker posing as Superintendent Diana Greene, just two weeks after the IRS issued the alert about W-2 phishing scams targeting school districts and nonprofits.
In some cases, fraudsters have followed up with an email from the alleged executive to payroll or the comptroller requesting a wire transfer to the scammer’s account—the most common end-goal of BEC schemes. When coupled with the W-2 scam, this means that some companies have lost both employees’ W-2s and thousands of dollars from wire transfers.
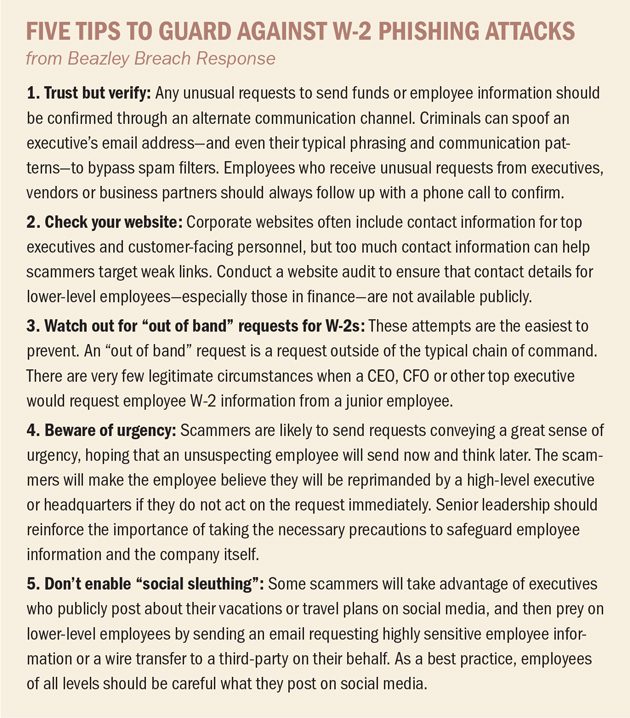
Indeed, Katherine Keefe, global head of Beazley Breach Response Services, reported that her team saw 35 of these scams in January and February 2017—twice as many incidents as last year. Losses ranged from just a few thousand dollars into the millions, she said.
Cyber insurance policies may offer some relief for companies that fall victim to these schemes. While cyber coverages can differ significantly, a cyber policy will generally respond when an organization suffers a compromise of personally identifiable information, according to Tim Francis, enterprise cyber lead at Travelers. “It doesn’t really matter if the information is obtained because someone hacked into the computer system or because an employee was fooled into sending out the information as part of a W-2 scam,” he explained.
In such cases, Francis said, a cyber policy may help the company by providing access to legal counsel that specializes in data and privacy events, notification and credit monitoring for impacted employees, and computer forensics experts to determine the full scope of the event.
Companies with active cyber insurance policies can not only get response assistance in the event of an incident, but may also be able to take advantage of their insurers’ resources to help proactively guard against the risk of W-2 phishing scams. “Cyber policies can provide protection by covering many of the costs that often go hand-in-hand with these events, but perhaps more importantly, a good cyber carrier is going to have access to a network of cybersecurity professionals that can provide expert assistance to help an organization deal with an event,” Francis said. “Additionally, most cyber carriers will offer access to information on best practices for helping prevent these events from happening in the first place.”
Companies that have fallen victim to these schemes often advise affected employees to file their taxes as early as possible, and indeed, one of the best ways to prevent the broader problem of tax refund fraud is to file before fraudsters can. Last year, the Federal Trade Commission reported that tax refund fraud was by far the biggest contributor to a 47% surge in identity theft complaints in 2015.
That trend shows little sign of abating, nor does the booming business of BEC attacks. In a February report by Vanson Bourne and email management firm Mimecast, 76% of C-level executives and IT decision-makers surveyed said their organization has security technology in place that is designed to prevent email impersonation fraud. But technology can only do so much when it is a human relationship being hacked—64% of respondents said their organization still suffered losses last year due to email impersonation. Of those, 34% suffered a data loss, 27% a financial loss, and 30% a loss of reputation.
In general, respondents expressed serious doubt about management’s ability to protect against email impersonation. Almost half thought their organization’s management team did not know enough about CEO fraud schemes to protect against the risk.
